Satellite communication is the process of conveying information between locations through the utilisation of communication satellites positioned in orbit around the Earth. The seamless experience of enjoying the English Premier League every weekend with friends would have been unattainable without the presence of these communication satellites. An essential component of this system is the communication satellite, an artificial satellite equipped with transponders that facilitate the transmission of signals. This technology establishes a communication channel connecting transmitters and receivers situated at distinct Earth locations.
The applications of satellite communication are widespread, encompassing telephone, radio, television, internet services, and military operations. Remarkably, there are over 2000 artificial satellites traversing the space just above us.
Each satellite serves a specific purpose and is positioned in diverse orbits. In this context, an orbit refers to the trajectory that a satellite follows as it revolves around a celestial body. Let's delve into a closer examination of the various types of orbits employed in satellite communication.
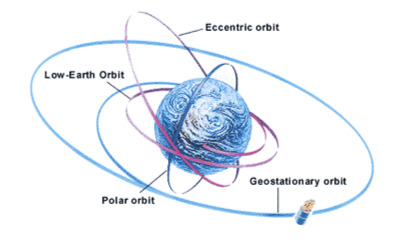
LOW EARTH ORBIT
Low Earth Orbit (LEO) is a circular orbit situated at an altitude ranging from 160 to 2000 km above the Earth's surface. The advantageous features of LEO include its low altitude and circular orbit, enabling it to complete revolutions around the Earth in approximately 90 minutes. Due to their close proximity to the Earth and the swiftness of their orbits (circling the globe in just 90 minutes), these satellites offer a line of sight spanning about 1000 km. Notably, LEO satellites travel at remarkable speeds, achieving an "Around the World in 90 minutes" phenomenon.
To ensure continuous connectivity for ground stations on Earth, a multitude of LEO satellites is essential. Despite their need for numerous satellites, LEO satellites offer several advantages. They are relatively easy to launch, and their proximity to the Earth means they do not necessitate high signal strength, presenting a significant benefit. Moreover, LEO satellites can be organised into satellite constellations, forming and maintaining specific arrangements relative to other satellites. This strategic constellation setup enhances the overall efficiency and capabilities of the satellite network in low Earth orbit.
MEDIUM EARTH ORBIT
A Medium Earth Orbit (MEO) satellite is positioned in orbit around the Earth at an altitude ranging between 2000 and 35786 km above the surface. Unlike Low Earth Orbit satellites, MEO satellites take more time to complete orbits, typically requiring 3 to 12 hours for one revolution. This extended orbital period results in longer visibility durations compared to their LEO counterparts.
The elevated position of MEO satellites, being higher up than LEO, contributes to improved coverage of the Earth's surface. This advantage is particularly beneficial for communication services that require broader geographical reach. However, it's important to note that the higher altitude of MEO satellites introduces certain drawbacks. The increased distance leads to longer communication delays and weaker signal strength, impacting the efficiency of real-time communication. Despite this limitation, MEO satellites strike a balance between coverage and signal performance, making them suitable for various applications, including global communication and navigation services.
GEOSTATIONARY ORBIT
A satellite positioned in a geostationary orbit around the Earth, approximately 35786 km above the surface, would appear stationary to an observer on the ground. This is due to the synchronisation of the satellite's angular velocity with that of the Earth. Both the Earth and the geostationary satellite cover 360 degrees in 24 hours, resulting in the satellite seemingly fixed in the sky relative to the observer.
The advantage of having a geostationary satellite is that it eliminates the need to constantly track the satellite's movement. Once the equipment is initially pointed towards the satellite, there's no requirement for further adjustments. While the process of placing a satellite in geostationary orbit involves significant expenses and complex equipment, this investment is offset by the convenience it offers in certain applications.
In applications such as Direct-to-Home (DTH) television services, the benefits of geostationary satellites are particularly notable. The transmission from the satellite can be scaled to reach a large audience, and the reception equipment on the ground is relatively inexpensive. This combination of fixed positioning and cost-effective reception equipment makes geostationary satellites a preferred choice for broadcasting services, where a stable and widespread signal coverage is crucial.
CYBER SPACE
The term "Cyber" pertains to the realm of computers, information technology, and virtual reality. Cyberspace is formed by the interconnected internet ecosystems. The challenges faced by cyberspace pose significant issues, necessitating the development of cybersecurity measures.
Cyberspace Faces Threats From
Interconnectedness of Sectors
The interconnected nature of various sectors within cyberspace creates vulnerabilities. As systems and networks become increasingly interlinked, a breach in one sector can potentially impact others, highlighting the importance of robust cybersecurity measures to mitigate such risks.
Increase in Exposure Points
The expanding digital landscape results in a higher number of exposure points. As more devices and systems become interconnected, the potential entry points for cyber threats multiply. This heightened exposure underscores the need for comprehensive cybersecurity strategies to safeguard against a variety of potential vulnerabilities.
Concentration of Assets
The concentration of valuable assets within cyberspace makes it an attractive target for malicious actors. Whether it's sensitive information, financial resources, or critical infrastructure, the concentration of such assets increases the severity of potential cyber threats. Implementing effective cybersecurity measures is crucial to protect these concentrated assets from unauthorised access and exploitation.
CYBER THREATS
Over time, various types of cyber attacks have evolved, each posing unique threats to digital environments:
Virus
A type of malware that self-replicates and spreads by inserting copies of itself into other executable code or documents, potentially causing widespread damage to systems.
Hacking Websites
Unauthorised access to websites, whether personal or professional, can lead to data breaches, loss of sensitive information, and compromise the security of the targeted site.
Malicious Codes
Security threats involving harmful code within software, which can breach system security and inflict damage on the targeted system.
Advanced Worm and Trojan
Malware disguised as legitimate software that, upon access, can cause damage to hard drives, disrupt background systems, and corrupt allocation systems.
Identity Theft and Phishing
Cyber attacks involving fraudulent emails that pose as legitimate entities, aiming to deceive individuals into revealing personal and professional information.
DOS, DDOS
Denial-of-Service (DOS) attacks and Distributed Denial-of-Service (DDOS) attacks involve overwhelming a machine or network with superfluous requests, rendering services unavailable by overloading systems.
Cyber Espionage
The illicit use of computer networks, particularly targeting government or important organisational privacy, to gather confidential information without authorization.
Cyber Warfare
Deliberate attacks on information systems using computer technology to disrupt a state's activities, especially for military purposes, with the intent of causing strategic disruptions.
(FAQs) – Satellite Communication and Cybersecurity
1. What is satellite communication?
Ans. Satellite communication is the process of transmitting information between locations using communication satellites in Earth's orbit. These satellites establish communication channels, connecting transmitters and receivers at different Earth locations.
2. How do communication satellites work?
Ans. Communication satellites, equipped with transponders, facilitate signal transmission by creating communication channels between transmitters and receivers on Earth. These satellites play a crucial role in various applications such as telephone, radio, television, internet services, and military operations.
3. How many artificial satellites are there in space?
Ans. There are over 2000 artificial satellites orbiting the Earth, serving different purposes and positioned in diverse orbits.
4. What are the advantages of Low Earth Orbit (LEO) satellites?
Ans. LEO satellites, with an altitude of 160 to 2000 km, offer advantages such as quick orbital revolutions (circling the Earth in about 90 minutes), ease of launch, and lower signal strength requirements due to their proximity to the Earth.
5. What distinguishes Medium Earth Orbit (MEO) satellites?
Ans. MEO satellites, positioned between 2000 and 35786 km, provide extended orbital periods, leading to longer visibility durations. They offer improved coverage for communication services but may experience longer communication delays.
6. How does a geostationary orbit benefit satellite communication?
Ans. In a geostationary orbit at approximately 35786 km, a satellite appears stationary to an observer on the ground due to synchronisation with Earth's angular velocity. This fixed position eliminates the need for constant tracking and is advantageous for applications like Direct-to-Home television services.
7. What is cyberspace?
Ans. Cyberspace encompasses the culture of computers, information technology, and virtual reality. It is formed by interconnected internet ecosystems, and ensuring its security requires cybersecurity measures.
8. What are the major threats to cyberspace?
Ans. The threats to cyberspace include the interconnectedness of sectors, an increase in exposure points, and the concentration of valuable assets, all of which underline the need for robust cybersecurity measures.
9. What types of cyber threats exist?
Ans. Various cyber threats include viruses, hacking of websites, malicious codes, advanced worms and Trojans, identity theft and phishing, Denial-of-Service (DOS) and Distributed Denial-of-Service (DDOS) attacks, cyber espionage, and cyber warfare.
10. How can cybersecurity protect against these threats?
Ans. Cybersecurity involves implementing measures to safeguard against unauthorised access, data breaches, and disruptions. This includes using firewalls, encryption, multi-factor authentication, and regularly updating security protocols to mitigate evolving cyber threats.

